Still confused about SSH public and private keys?
Blake Smith's 2010 article, "understanding public key private key concepts" provides the absolute best analogy I've come across.
This brief article lays it as simply and memorably as it gets.
DocSalvage Info
... Trust in truth keeps hope alive
SSH keys beautifully explained

Understanding how SSH keys work and how to properly use them has long baffled even some of the most venerable programmers.
In the physical world, a given key usually fits just one lock. We have to special order multiple locks keyed the same for entry doors and such. To share access to something, we give out multiple copies of these physical keys.
It's thus tempting to imagine the shared "public key" to be analogous to a physical key and the "private key" to be the lock.
Actually, it's the other way around.
Wogan explains in "How to set up public key ssh authentication" (January, 2014).
Itching Ears
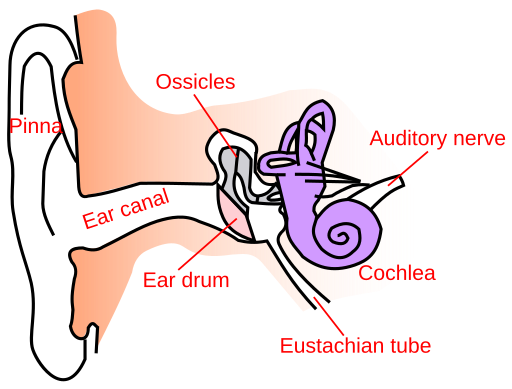
And now for something completely different...
A friend asked me about this recently and I responded with a lot of detail. Posting it here so I don't lose it. Hope it helps someone.
How do I treat persistently itching ear canals?
I have been fighting with the same problem for several years. Tried everything. Read a lot. Here's what works best for me...First... have found no permanent solution. Just treatments that have to be repeated every few days.
Second... most common cause of itching is soap/shampoo in the ears. Use the mildest thing you can when washing hair and face and dry out ear canals well afterward. I even use blow dryer for this. Dermatologist got me on Dove Sensitive Skin bar soap years ago and I use it in place of shampoo as well. It contains more oils than any other soap. Lather once to remove grease (sweat and hairspray). Rinse. Lather again to put oils back in that make hair smooth and soft (not stuck together). Rinse.
On Q-tips... Without them, this problem is pretty much only treatable by a physician (read: expensive). Since the Rich are preventing Democrats from having the money for constant medical care, we are left to our own devices. Read on...
On Q-Tip Safety...
1) NEVER use Q-Tips on someone else because you cannot know when you reach the eardrum. I dated a girl years ago whose mother cleaned her ears out with hydrogen peroxide regularly. Her eardrum had been punctured for years and we paid for her to have surgery to rebuild it because her Pentecostal parents refused to. Hydrogen Peroxide is good for lots of things, but I'm not a fan of using it on semi internal mucus membranes like ear canals.
2) NEVER use both ends of the Q-Tip in different ears! That just gives you 2 ears itching instead of 1 at a time. Don't know why they continue to make them double-ended other than the cotton ball makes it easier to hold onto.
3) Insert Q-tip VERY SLOWLY into YOUR OWN EAR with slight pressure against roof of ear canal. Gravity makes wax collect on floor of canal.
4) Listen for the individual threads sticking out from Q-Tip to start brushing your eardrum and STOP when you hear/feel them. NEVER PUT PRESSURE ON EARDRUM. It hurts and it can puncture it. If punctured, water from washing/swimming will enter middle-ear which will cause the most painful infection you've ever experienced.
5) On reaching the eardrum, press down LIGHTLY and pull out, using the Q-Tip to pull the wax out of ear.
On Treating the Itch...
What we just did irritates the ear canal, so actually can make itch worse. But we need fairly clean canal in order to treat it.
Apply any of the following to one end of a clean Q-Tip and gently swab the ear canal:
For intense itching, can use antibiotic plus pain reliever cream. It's the pain reliever that actually stops the itching and the cream soothes the irritated skin. Haven't found a non-antibiotic formulation of this though. Cream is better than ointment because it soaks in.
Next most effective is Chest Rub (Vicks VapoRub or Metholatim). VapoRub and generic Chest Rub are just petroleum jelly (Vaseline) with 2.6% menthol in it. The jelly moisturizes the skin and protects it from fungus and bacteria. It's the natural menthol that treats the itching. The greater the percentage menthol the more effective -- BUT too strong burns, thus making it worse. 2.6% seems okay for ears. Can use stronger concentrations for flea bites, etc. on extremities as that skin is tougher. Most muscle "hot/cold" sprays and such as just high concentrations of menthol (12-16%). Do Not Use In Ears!
For maintenance and minor itching, can just use plain petroleum jelly or any oil like Mineral Oil (very cheap) or olive oil. They used to sell little bottles of "sweet oil" for ears but it was just olive and/or mineral oil I think.
Homophobia and Homosexuality
 |
| PaintingOnScars.com |
This pretty credible source substantiates the reports on the Harvard/MIT and other studies that show a strong correlation between homophobia and suppressed homosexual feelings.
As Freud found, and with it launched the discipline of psychology... it is the intense suppression of true feelings that causes harmfully abnormal stress and behavior; not the feelings themselves.
The whole process of growing up and "becoming civilized" is the process of learning to suppress true feelings when they are harmful to others. This is the mandatory requirement in order to have any kind of functional society.
However, looking deeper tells us that (like everything) there are limits.
Too much suppression, too intensely, for too long creates a fragile psyche that can collapse into harmful behavior when stressed.
Climate Change is a Huge Business Opportunity
 Climate-change is the greatest business opportunity since the American westward expansion of the 1800s.
Climate-change is the greatest business opportunity since the American westward expansion of the 1800s.American unbridled imagination could lead the world in adapting to it.
That is, if government stopped coddling businesses already making more profits than they know what to do with on financially safe, but dirty and wasteful, old technologies.
As the seas rise and the weather worsens over the next few decades, millions of structures will be damaged and flooded. How are we going to preserve and protect them?
Weather is becoming more extreme. Tornadoes more frequent. Hurricanes farther north and earlier in the year. Unusually high winds. Dry thunderstorms igniting fires. Sudden snow storms out of season. How do we adapt to this new normal?
We need creative thinking. Roofing materials must be redesigned to withstand higher winds and bigger hail. Homes and high-rises must be reinforced. Building codes require massive overhaul to allow for the new approaches and new materials.
Established industries that refuse to adapt will fail. New business models will require a deferment of short-term profits. Owners and stock-holders must be willing to invest in risky new technologies that are not as profitable today but have the best chance to prevail in the future.
Solar panel technology is advancing almost as fast as computers. It will soon be cheaper to produce electricity at the point of use rather than a central location. Utility companies that embrace that fact will prosper by providing standardized, reliable point-of-use systems. Such systems could use of the existing transmission infrastructure for load-balancing and second-sourcing.
The most dramatic reduction in energy use and pollution may not even come from solar panels and electric cars, but instead from a better Internet.
Why do we consume vast amounts of energy and pour out tons of pollution to drive across town twice a day? Why do we leave one perfectly good building empty, only to occupy another? Most jobs today are information workers who could be located anywhere. Why not at home?
That means renovations to create better home-offices. Installation of higher speed Internet and faster computers. More sound-proofing. More ergonomic chairs.
It also means renovating office buildings into apartments. Maybe more two-car driveways to accommodate service vehicles parked at the technician's home while off-duty instead of in a big parking lot.
More extreme weather means more damaged roofs and broken windows. Flat video displays that use very little power are now common and rapidly getting cheaper and more efficient. Digital cameras likewise. For safety, energy conservation and your choice of views, why not "virtual-windows"?
The massive upheavals caused by climate change will create unprecedented economic opportunities... for those ready and willing to embrace it.
photo credit: Climate Indicators - Relative Sea Level Change Along U.S. Coasts via photopin (license)
Interview with Michael Tiemann, open source pioneer
via Bryan Behrenshausen (Red Hat) at opensource.com on 05 Aug 2014
"There are many who have tried to bring the zero-sum game concepts to the open source community," Tiemann says. "They want to wall off some piece of technology, at least from a positioning point of view. They want to force everybody into that particular worldview."Fascinating interview. Fascinating concepts… for software development (as well as finance)…
“Picture a bank, he said, that pays to every one of its patrons an amount of interest based on the sum of all the money it contains.
"In the conventional world, a bank pays interest based on the amount of money that’s deposited. But imagine a bank where no matter how much you deposit, the bank pays interest on the sum total of all the assets to which you make the deposit. So if a whole bunch of my friends all put money into a communal bank account, and then we all get paid the total interest on that sum total, how attractive is that?”
Your Vote Does Not Count
I believe most programmers can't help but fear that the outcome of elections for many years have been determined largely by incumbent politicians, bureaucrats and the handful of election software companies... all of them highly conservative.
While there is probably still enough restraint to allow a landslide vote the other way to prevail, my own sense is that most single-digit victories probably are fraudulent.
Democratic elections require transparent and verifiable election software at all levels. None is currently allowed in any binding election in this country today.
The reaction to the 2000 presidential election debacle was a masterful use of a crisis to set in motion a campaign to strip away most of the civil rights gains of the last 50 years.
Your vote doesn't count, and neither does mine, until this "electronic ballot-stuffing" is ended.
While there is probably still enough restraint to allow a landslide vote the other way to prevail, my own sense is that most single-digit victories probably are fraudulent.
Democratic elections require transparent and verifiable election software at all levels. None is currently allowed in any binding election in this country today.
The reaction to the 2000 presidential election debacle was a masterful use of a crisis to set in motion a campaign to strip away most of the civil rights gains of the last 50 years.
Your vote doesn't count, and neither does mine, until this "electronic ballot-stuffing" is ended.
Some Favorite Quotes

"It's not that I'm so smart, it's just that I stay with problems longer."
Albert Einstein
"In a time of universal deceit, telling the truth is a revolutionary act."
widely attributed to George Orwell
http://en.wikiquote.org/wiki/George_Orwell
"The price of freedom, is eternal vigilance."
Leonard H. Courtney, Thomas Jefferson, Jean-Luc Picard (fic.), et.al.
"A rising tide sinks all boats that are anchored to the bottom."
“Nothing in all the world is more dangerous than sincere ignorance and conscientious stupidity.”
Rev. Martin Luther King Jr.
Albert Einstein
"No problem can be solved from the same level of consciousness that created it."
Albert Einstein
"Everything that can be counted does not necessarily count; everything that counts cannot necessarily be counted."
Albert Einstein
"Any man who reads too much and uses his own brain too little falls into lazy habits of thinking."
Albert Einstein
"Education is what remains after one has forgotten what one has learned in school."
Albert Einstein
"Logic will get you from A to B. Imagination will take you everywhere."
Albert Einstein
"Whoever is careless with the truth in small matters cannot be trusted with important matters."
Albert Einstein
"That is the way to learn the most, that when you are doing something with such enjoyment that you don’t notice that the time passes."
Albert Einstein, 1915
"Any intelligent fool can make things bigger, more complex, and more violent. It takes a touch of genius - and a lot of courage - to move in the opposite direction."
Albert Einstein
"The optimist proclaims that we live in the best of all possible worlds; and the pessimist fears this is true."
Branch Cabell, author of satirical fantasy
"Perfection is achieved, not when there is nothing more to add, but when there is nothing left to take away."
Antoine de Saint-Exupery, French writer (1900 - 1944)
Shellshock Summary
DESCRIPTION
Twenty-five year old security flaw CVE-2014-6271 found in all versions of bash.
Per http://lcamtuf.blogspot.com/2014/09/quick-notes-about-bash-bug-its-impact.html
"The behavior is implemented as a hack involving specially-formatted environmental variables: in essence, any variable starting with a literal "() {" will be dispatched to the parser just before executing the main program. You can see this in action here:
$ foo='() { echo "hi mom"; }' bash -c 'foo'hi mom
NOTES
- 2014-09-25 14:55:22 Experiments indicate that putting anything in front of the
(), like a name for the function or the keywordfunction, disable the flawed behavior - 2014-10-04 05:02:11 Calling bash from ash still passes all the commands in the variable(s)
RESOURCES
- CVE-2014-6271
- http://lcamtuf.blogspot.com/2014/09/quick-notes-about-bash-bug-its-impact.html
- http://unix.stackexchange.com/questions/157381/when-was-the-shellshock-cve-2014-6271-bug-introduced-and-what-is-the-patch-th?rq=1
- http://unix.stackexchange.com/questions/157329/what-does-env-x-something-bash-c-command-do-and-why-is-it-insecure
- http://www.engadget.com/2014/09/24/bash-shell-security-flaw/
Ayn Rand
Just watched Ayn Rand on Johnny Carson (1967)
This was not the usual late-night-talk-show guest interview. No jokes. Very serious. And went over into what was supposed to be another guest's time. (total of about 30mins)
If Ayn Rand were alive today and could speak for herself, I think she would vigorously denounce Rand Paul, Paul Ryan and the rest of her "neo-disciples"... and they would denounce her.
For example... In this interview, she very strongly asserts that no one has the right to another person's life. To that end, she clearly expresses her opposition to any draft for any reason. Only individuals have the right to decide to risk their lives.
Seems to me that the Republicans have hijacked some of her philosophies (primarily laissez-faire capitalism) to justify destroying the lives of others in furtherance of their own affluence.
This interview indicates that in her philosophy of Objectivism, she expected everyone to vigorously pursue their own self-interest. To me, the flaw in it was that she seemed to think everyone had roughly the same capacity to do that. We know that they don't. But at the time of the interview (1967), the divergence was far smaller than it is today.
I couldn't disagree more with today's Republican interpretation of Ayn Rand's philosophies. I could say the same about the Christian churches' interpretation of Jesus' philosophies. I think both have been used to further agendas that each would abhor were they alive.
Perhaps that's why these "reinterpretations" have only come about well after the icons were too dead to disagree.
Subscribe to:
Posts
(
Atom
)




